
Cleared cookies yet still recognized? That’s browser fingerprinting: sites blend small device and browser details into a unique profile. It helps with security and fraud, but raises privacy concerns. Learn how it works and how to limit exposure.
HTTP Proxies are handling HTTP requests towards the internet on behalf of a client. They are fast and very popular when it comes to any kind of anonymous web browsing.
Let our premium DNS servers solve your queries and unblock a lot of geo-restricted content that is often blocked using DNS-based identification techniques.
Browser fingerprinting is a way for a website to recognize a device without saving anything on it. Instead of dropping a cookie, the site watches how your setup looks and behaves. It notices your browser version, screen size, graphics pipeline, fonts, language and time zone, which codecs you support, and even how your audio system processes a tiny test sound. Put together, those little clues form a profile that’s distinctive enough to match you when you come back.
Two ideas make this powerful. There’s nothing local to erase, because the profile is rebuilt from scratch every visit. And while any single detail is ordinary, the combination is rarely shared. Plenty of people use your screen size or language, but far fewer share your exact mix of GPU, driver, fonts, codecs, and preferences.
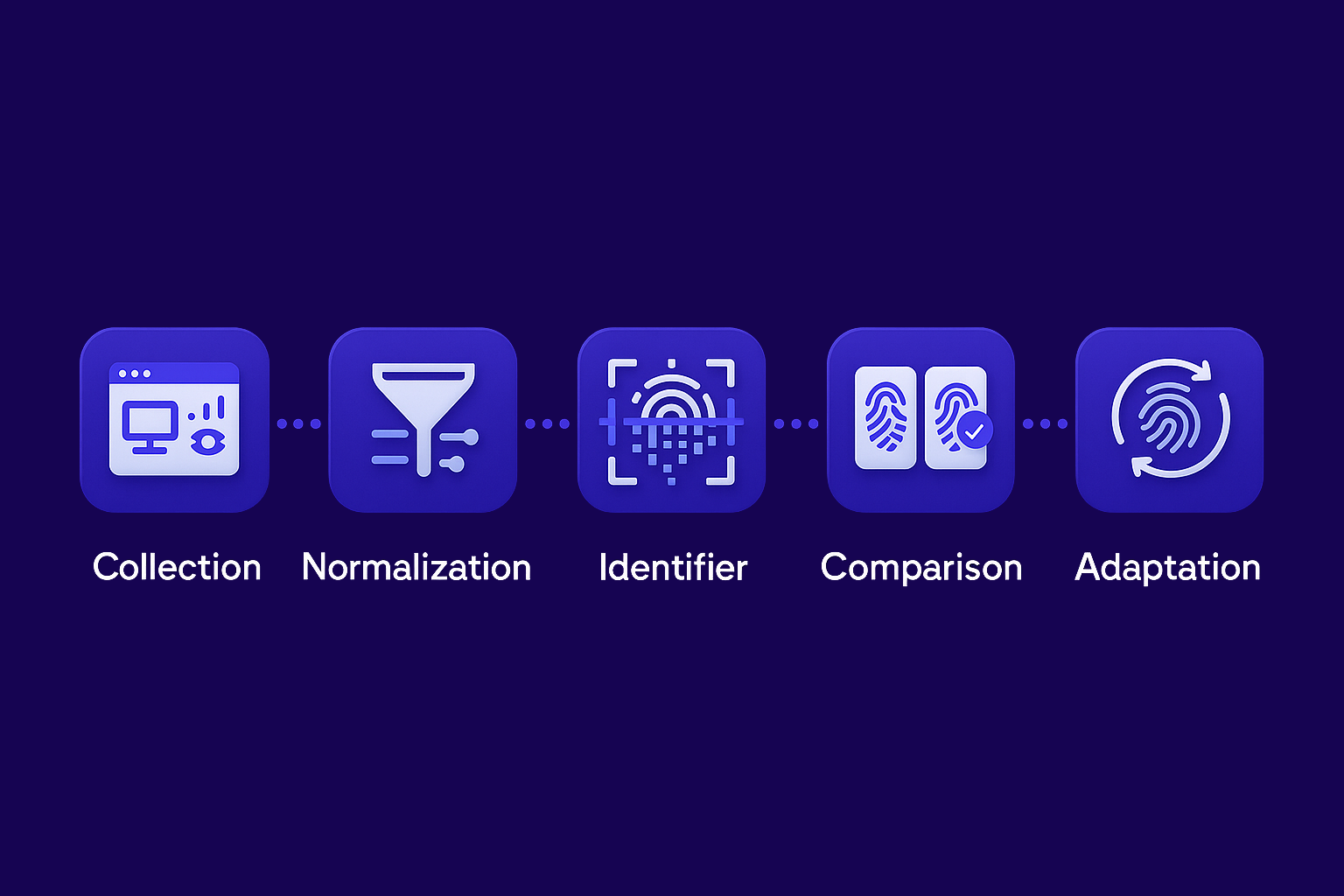
First, signals are collected. When a page loads, basic details arrive automatically with the request. Then the site may ask the browser a few quiet questions through high-entropy programming interfaces like Canvas, WebGL, and the AudioContext to capture rendering and timing quirks.
Next, values are normalized. Text is cleaned, numbers may be rounded, and noisy fields are stabilized so tiny fluctuations don’t cause false mismatches from one visit to the next.
Then, an identifier is derived. All those features are combined and often hashed into a compact fingerprint that’s easy to store and compare.
After that, the new visit is checked against what’s on file. The current feature set is scored against past ones, and the system decides whether it’s likely the same device or a different one.
Finally, profiles adapt. Many systems update the stored template as your setup evolves, keeping recognition steady even when you make minor changes.
Sites rarely rely on a single signal. They layer many small clues until the combined picture looks distinctive. Let's see below what are some of the most common methos used for fingerprint tracking.
Every request carries basic facts such as your internet protocol address, the protocol version in use, the order of headers, your language, and your preferred encodings. These are ordinary on their own, yet they help set the baseline. If you are choosing how to route traffic, it helps to understand how HTTP vs SOCKS proxies changes the way your connection appears.
Your screen resolution, device pixel ratio, color depth, refresh rate, and whether your device supports touch or advanced pointer input all contribute small bits of uniqueness. Even memory hints can make one setup look different from another.
A page can quietly draw text or shapes on an HTML canvas and read the numeric result. The outcome varies across devices because of your graphics card, driver version, font rasterizer, and antialiasing methods. Those tiny differences tend to be stable enough to recognize again later.
WebGL reveals how your graphics pipeline handles shaders and precision. When those results are paired with canvas measurements, the combination becomes more identifying than either method alone.
By generating a short, inaudible tone and measuring how your audio stack processes it, scripts can capture small timing and rounding quirks. These values are not dramatic, but they are surprisingly consistent from visit to visit.
Pages can infer which fonts you have by attempting to render specific families and by measuring glyph widths. A custom or uncommon font set adds noticeable distinctiveness to your profile.
Headless operation, webdriver flags, stripped fonts, and very regular input timing can reveal automation. If you test or scrape, it pays to understand what signals your tools expose so you can configure them more carefully.
The resolver you use and the way it answers can hint at your location or network setup. If the resolver does not align with the location shown by your exit address, some sites will notice the mismatch.

A fingerprint is simply a structured bundle of details your device reveals during normal browsing. None of them feels sensitive in isolation. Together they create a surprisingly solid portrait. Below, you can see what information is inside a browser fingerprint.
These include your internet protocol address, the transport protocol in use, hints from the security handshake, and the domain name system resolver that handles your lookups. If you want the story your DNS tells to match your chosen location, route those lookups through DNS proxies so resolution aligns with your exit region..
Here you will find the browser family and exact build, the rendering engine, operating system clues, the WebGL vendor and renderer, how your audio stack behaves, which codecs you support, your time zone, your preferred languages, the Do Not Track preference, and whether motion reduction is enabled.
Screen dimensions, viewport size, color depth, device pixel ratio, number of touch points, pointer precision, and even gamepad presence can all appear in the profile.
Availability of LocalStorage and IndexedDB, the status of service workers, current permissions for things like notifications or sensors, and similar flags do not identify you on their own. They do refine the overall picture.
Patterns such as pointer movement, scroll rhythm, and page timing can act as a second opinion for fraud and abuse decisions. Responsible teams treat these as security signals rather than a way to track people for marketing.
Fingerprinting helps spot patterns that do not look human, even when someone keeps changing addresses. It flags multi account operations, stolen card testing, scripted checkouts, and other automated abuse. Because the device profile tends to stay similar from one attempt to the next, teams can connect actions that would otherwise look unrelated.
A familiar device profile is a positive signal during sign in. If you usually log in from the same browser and the same setup, that consistency supports trust. When a login arrives with a very different profile, the site can ask for a little more proof, such as a one time code or a security key, before letting the session continue.
Free tiers and trials are magnets for repeat signups. Recognizing the same device across resets discourages this cycle and helps protect resources. It also lets publishers enforce fair use without demanding heavy handed steps from genuine readers.
As third party cookies fade, some teams lean on device traits to estimate returning visitors and keep metrics stable. This is sensitive territory when it drifts toward cross site tracking. Anyone using it for measurement should set clear limits and communicate openly about what is collected and why.
Experiments only work when people stay in their assigned bucket. Device recognition keeps visitors in the same group across sessions, which reduces noise and makes test results more reliable.
It depends on where you are and how the data is used. A practical rule helps. If a fingerprint can single out a person or a device, many privacy laws treat it as personal data. That brings real responsibilities and there needs to be a valid reason to collect it, clear and plain disclosures, careful minimization, and respect for user rights where they apply. Keep in mind that this is a not legal advice, but the safest approach is to gather only what you truly need, use it only for the stated purpose, and be transparent from the start.
Proxies will not stop browser fingerprinting by themselves, but they do shape the biggest network clues a site sees. Think IP address, rough location, and DNS lookups. Pair the right proxy setup with sensible browser habits and you make tracking a lot harder without breaking your workflow. Below are some of the most useful points to do this.
Start simple. Route everyday traffic through HTTP proxies to mask your address while keeping tools and settings the same.
Scale when you need rotation. Use rotating datacenter proxies for speed, volume, and frequent IP changes when you are crawling or testing at scale.
Blend in when trust matters. Pick rotating residential proxies so requests inherit real household reputation for e-commerce checks, local results, and web scraping.
Keep DNS in sync with your exit. Align lookups with your chosen region using DNS proxies to avoid the classic mismatch of one country for IP and another for DNS.
Automate without noisy leaks. When you script tests or controlled data collection, route automation correctly with the Puppeteer proxy setup guide so Chrome uses your endpoints consistently.
Important note: Proxies change your network story by masking IP and location, but they do not alter your device fingerprint. In-browser traits such as canvas, WebGL, audio processing, and font lists remain visible. To lower uniqueness, keep your setup ordinary by using mainstream fonts and extensions, aligning locale and time zone, and separating activities into different browser profiles.
Modern sites can recognize a returning device from a mosaic of small signals. Trying to stop that by disabling JavaScript may block some probes, but it also breaks key features across the web. The realistic fix is a layered approach. Keep your setup ordinary, avoid unusual fonts or extensions, and keep time zone and locale consistent. Besides this, if you need proxies that match your needs, be sure that you take a look at our proxy services.
@2025 anonymous-proxies.net