
This article will show you how an Iran proxy beats the nation’s firewall, explain which proxy types still work under 2025’s restrictions, outline its use cases—from news access to payments—and guide you through a quick Windows setup so you can browse freely again in just a few minutes.
Shadowsocks is a secure and encrypted protocol encapsulating a SOCKS5 proxy. It is used mostly for bypassing censorship or other kind of internet filters.
A Proxy protocol which allows you to bypass even the strictest internet censorships or firewalls out there all due to a clever tactic applied when a connection is being applied
Wireguard version of the Amnezia VPN which is a more privacy-oriented VPN application designed to bypass even the most strict internet censorship regimes.
Since the reported Israeli air-strikes near Tehran on 13 June 2025, Iranian authorities have repeatedly flipped the nation’s “digital kill-switch.” NetBlocks’ live graphs tell a stark story: nationwide bandwidth has been throttled so hard that only a sliver—sometimes three or four percent—of normal capacity still drips through. For most people that means 24-plus hours in a digital blackout, where BBC Persian takes minutes to load (if it loads at all), Telegram messages hang in limbo, and banking apps freeze on the splash screen until the authorities decide otherwise.
Still, a technically adept minority continues to stream BBC Persian, back up files to the cloud, and video-chat with family abroad. Their advantage is not a loophole or luck; it is the use of an Iran proxy—a service that disguises data as ordinary HTTPS traffic and slips through deep-packet-inspection filters unnoticed. In this article, we will see exactly what Iran proxies are, which types of proxies are the best to get past Iran's firewalls, its use cases, and how you can set one up in minutes.
An Iran proxy is a discreet middle-man server that reroutes every click, tap, and upload through its own encrypted tunnel before handing the data back as if nothing out of the ordinary occurred. Each packet is wrapped to resemble routine HTTPS traffic, so Iran’s deep-packet-inspection gear has no distinctive pattern to block or throttle. From your laptop to the proxy node, the stream remains fully encrypted end-to-end, meaning watchdogs see only indecipherable cipher text—no web addresses, chat logs, or file names. In effect, the proxy becomes a hidden trapdoor in the firewall: you browse, stream, and converse as though the blockade never existed, all while your digital footprints stay safely out of sight.
When the state black-holes BBC Persian, Radio Farda, Telegram, X, and Instagram, an Iran proxy wraps every request in everyday HTTPS and pushes it through the filter. You can scroll live foreign headlines, join protest channels, and upload videos without your Iranian IP betraying who—or where—you are.
Stripe, PayPal, and Wise refuse traffic from Iranian subnets, freezing freelance income and export sales. Routing dashboards and API calls through an Iran proxy makes the session appear to originate from a compliant region, so invoices clear and foreign customers keep buying even when new sanctions roll out.
During crackdowns, censors throttle ports used by YouTube, Netflix, Zoom, and WhatsApp VOIP. An Iran proxy tunnels those data streams inside innocuous TLS traffic, restoring HD playback and crystal-clear video calls so families, students, and activists can talk and broadcast in real time.
Access to Google Scholar, Springer journals, GitHub, AWS consoles, and sensitive health sites often vanishes overnight. By funnelling research queries, repo pushes, and medical pages through an Iran proxy, scholars and patients regain the full web while deep-packet inspection sees only encrypted noise—not the papers, code, or guidance being read.
The censorship engines sitting on Iranian backbones are tuned to hunt for familiar VPN hand-shakes, fixed ports, and recognizable payload patterns. Two proxy protocols are built specifically to dodge those scans and the technical details in their own manuals explain why they still work. Below, we will tell you more about them.
Trojan proxy begins every connection with a real TLS handshake, exactly the sequence a normal browser runs when it visits any HTTPS site. After the handshake, the client sends an authentication hash and a SOCKS5-style request inside the encrypted channel; if that hash is wrong, the server simply forwards the traffic to a preset web endpoint, making the whole session look like ordinary HTTPS probing a public site. Because all invalid or suspicious probes are greeted by the same decoy site, active scanners have no reliable fingerprint to block. In practice, the firewall sees nothing more exotic than a certificate, a validated TLS session, something it hesitates to kill for fear of breaking online banking and government portals.
Shadowsocks proxy takes a lighter approach. Basically, it encrypts each TCP or UDP stream with modern AEAD ciphers and transmits data that is “indistinguishable from a random byte stream,” defeating deep-packet inspection outright. The client behaves like a local SOCKS5 server: it wraps your target address plus payload in the encrypted envelope, ships it to the remote node, and the node decrypts and relays it onward. Because no formal handshake or fixed port is required, operators can bolt optional plugins—WebSocket, simple-obfs, or any custom layer—on top, further blending the traffic into everyday CDN chatter.
Both technologies beat a classic VPN for one reason: OpenVPN, IKEv2, and even vanilla WireGuard reveal themselves through predictable byte sequences and dedicated ports. Once the Iranian DPI boxes match those patterns, the offending IP is throttled or null-routed within minutes. Trojan’s genuine TLS frontage and Shadowsocks’ cipher-only stream remove those patterns entirely, giving users the confidentiality of a VPN without the giveaway handshake.
Before you begin, sign in to your Anonymous-Proxies Dashboard and copy the credentials for the proxy you purchased—the server IP, port, password, and (for Trojan) the SNI host. You’ll paste these values in the steps below.
Go to the official Shadowsocks website, click the link labeled “shadowsocks-windows” under GUI Clients, and you’ll jump to its GitHub page.

Scroll down and click the blue “release page” link.
Then download the latest ZIP—usually named something like Shadowsocks-4.x.x.zip.
Extract the ZIP to any folder, open it, and double-click Shadowsocks.exe.
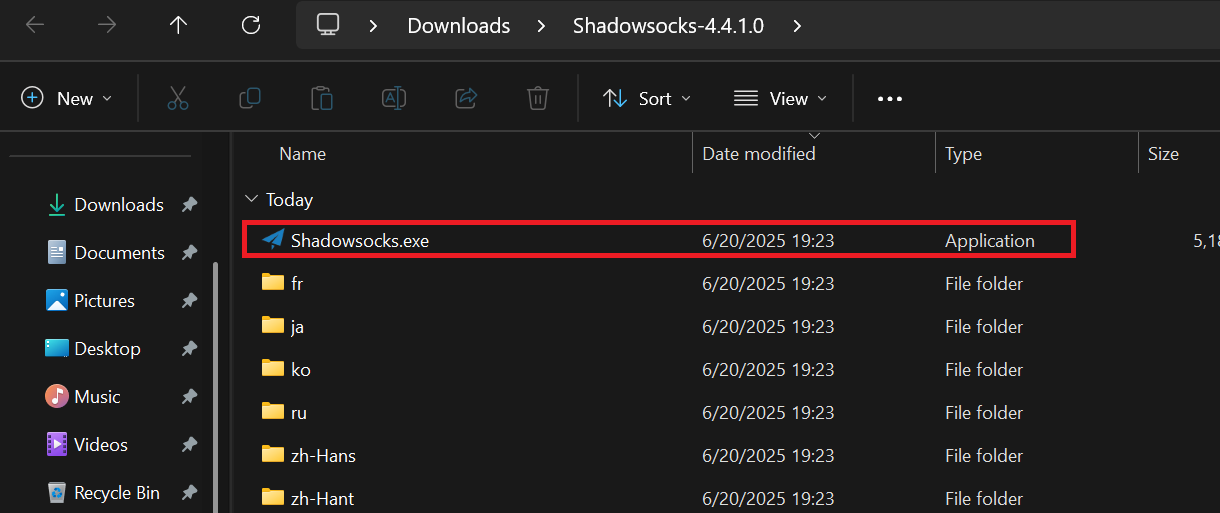
Once you opened the Shadowsocks client, you'll need to enter:
Click Apply and then OK.
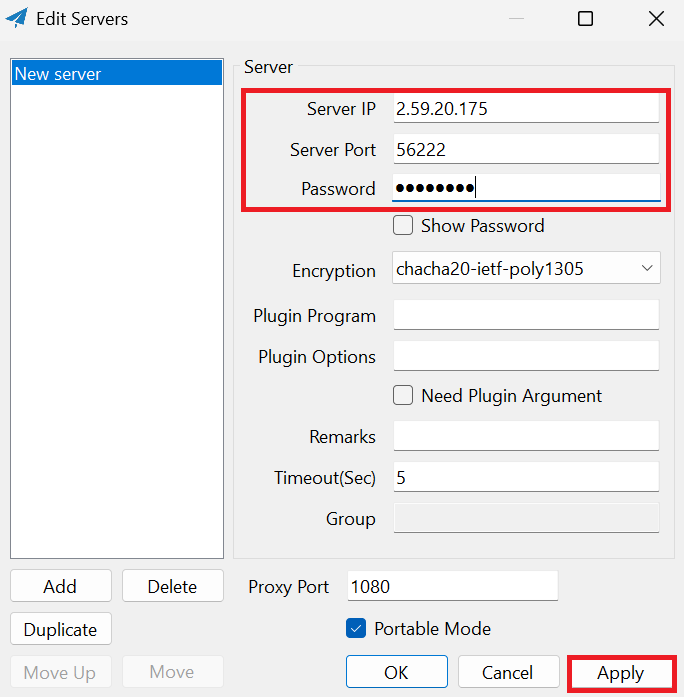
For the final step, you need to right-click the paper-airplane icon, hover over System Proxy, and select Global. Once you did this, a check-mark will appear next to Global, confirming Windows is now routing all traffic through the encrypted Shadowsocks tunnel.
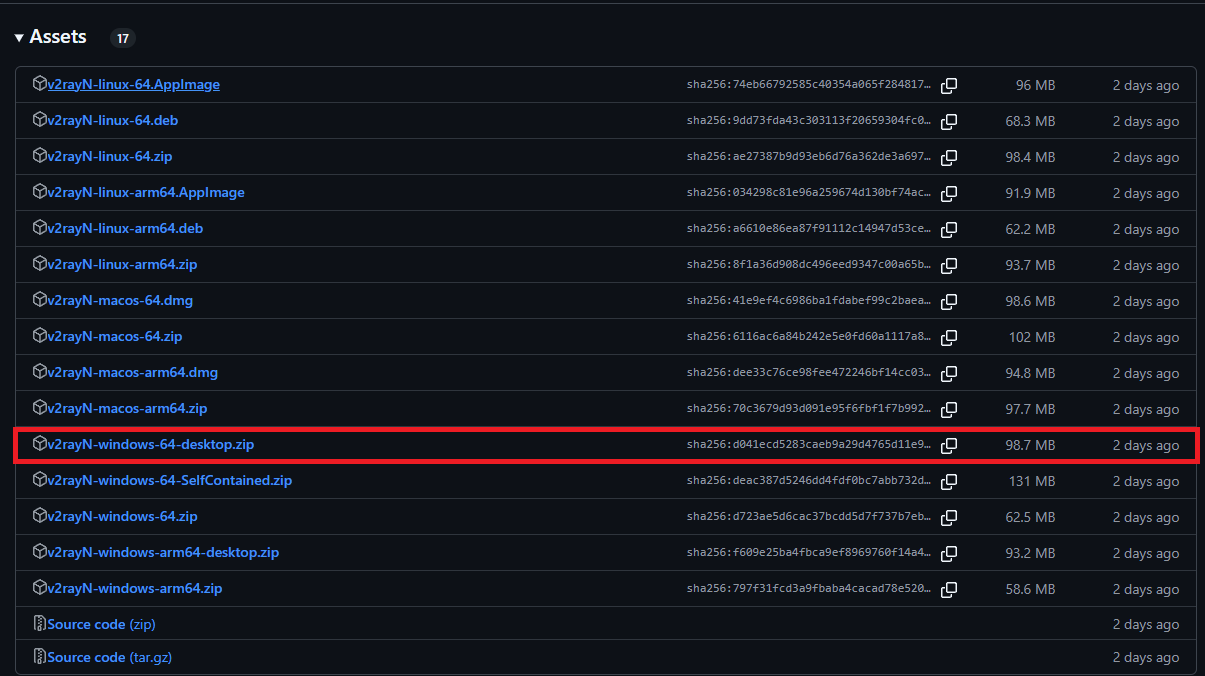
Open the V2RayN releases page, scroll to Assets under the latest release, and click the file named v2rayN-windows-64-desktop.zip.
Unzip the archive and launch v2rayN.exe.
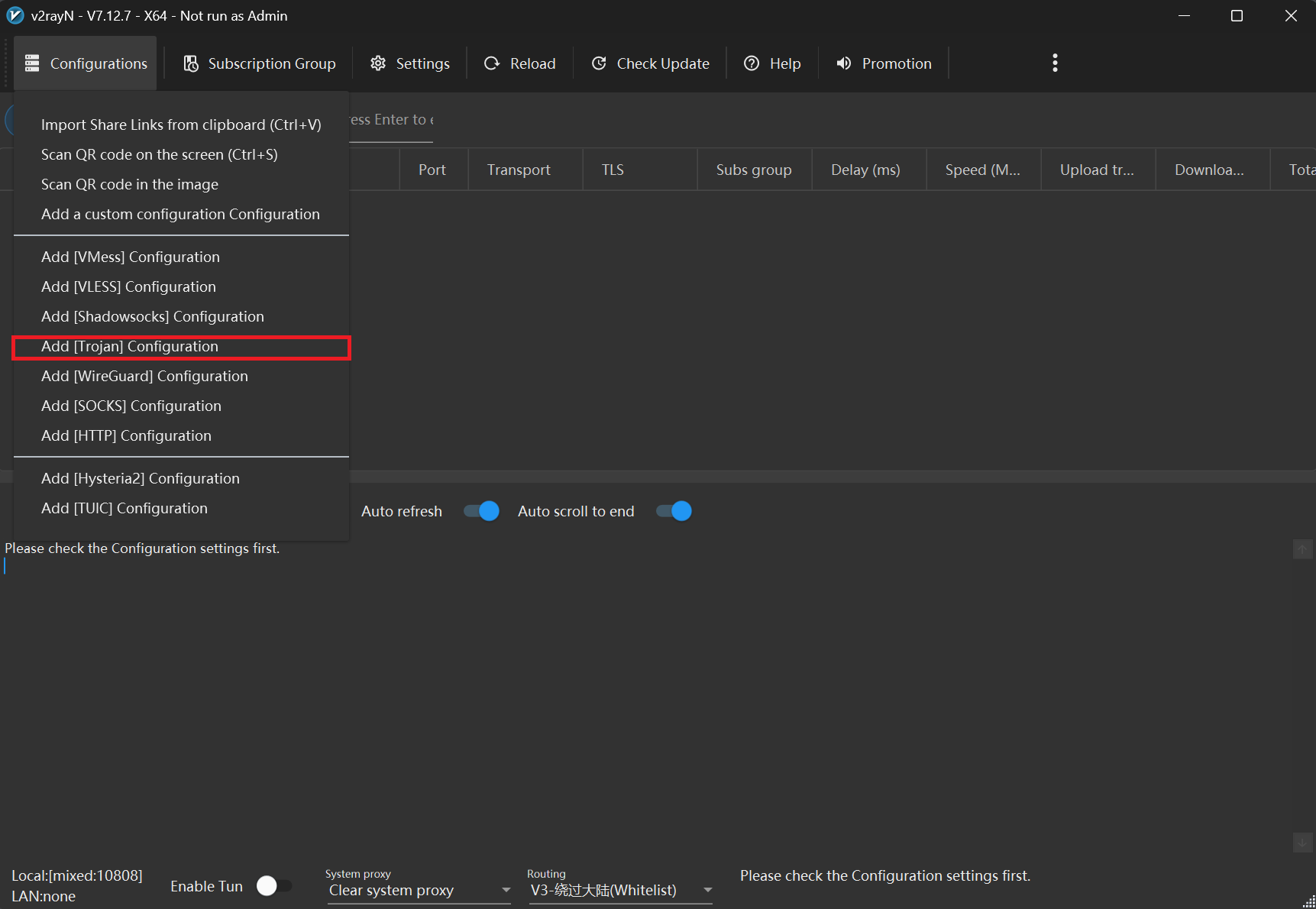
Click Configurations → Add [Trojan] Configuration.
Now a form should open and here you will need to introduce next details:
tcpnonetlsh2false
Click Confirm.
At the bottom bar, click on the System proxy dropdown and choose Set system proxy.
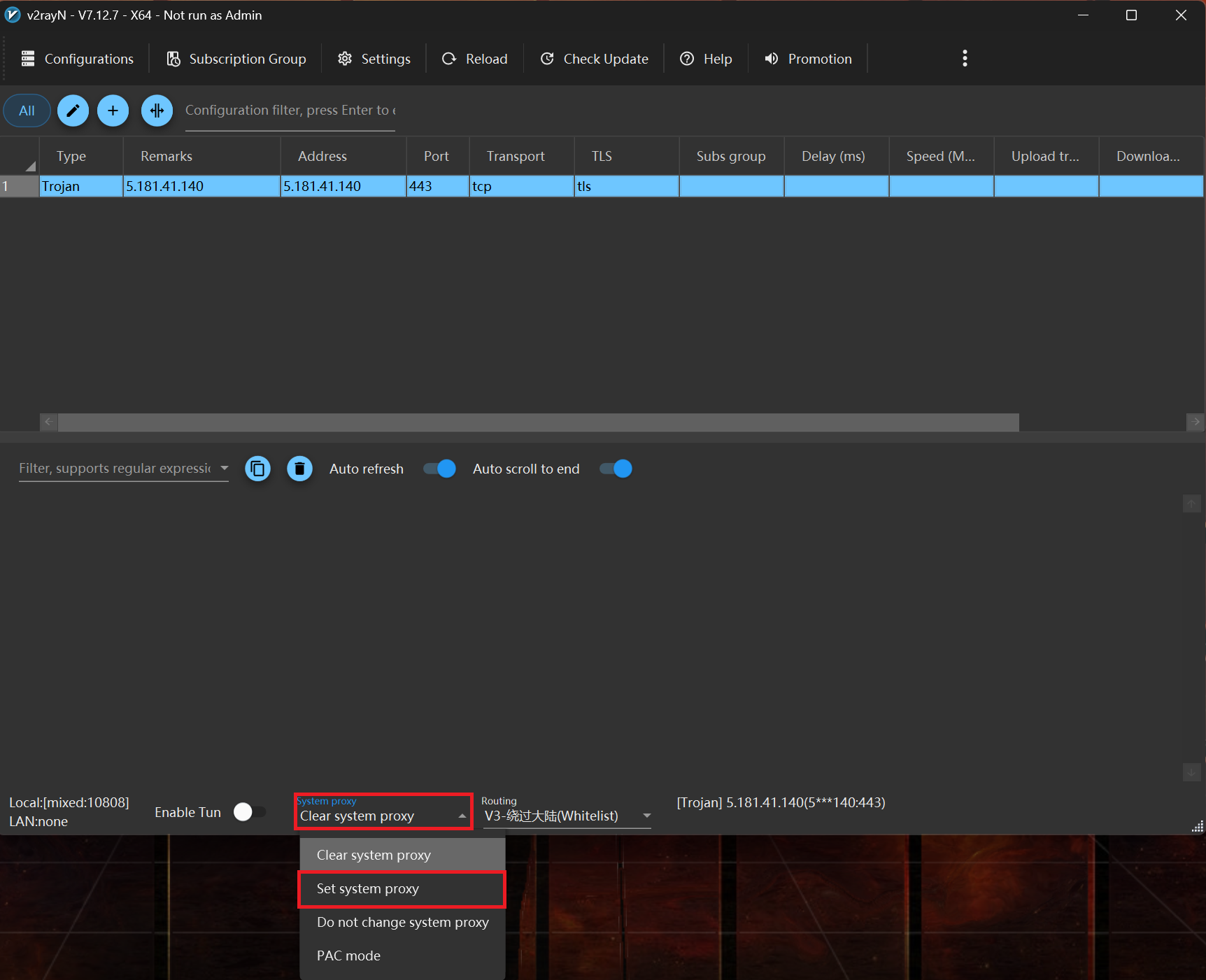
Next, open the Routing menu beside it and pick Global so every app routes through the tunnel.

All what remains to do is to toggle Enable TUN. Windows will prompt for permission to create a VPN interface; click Yes.
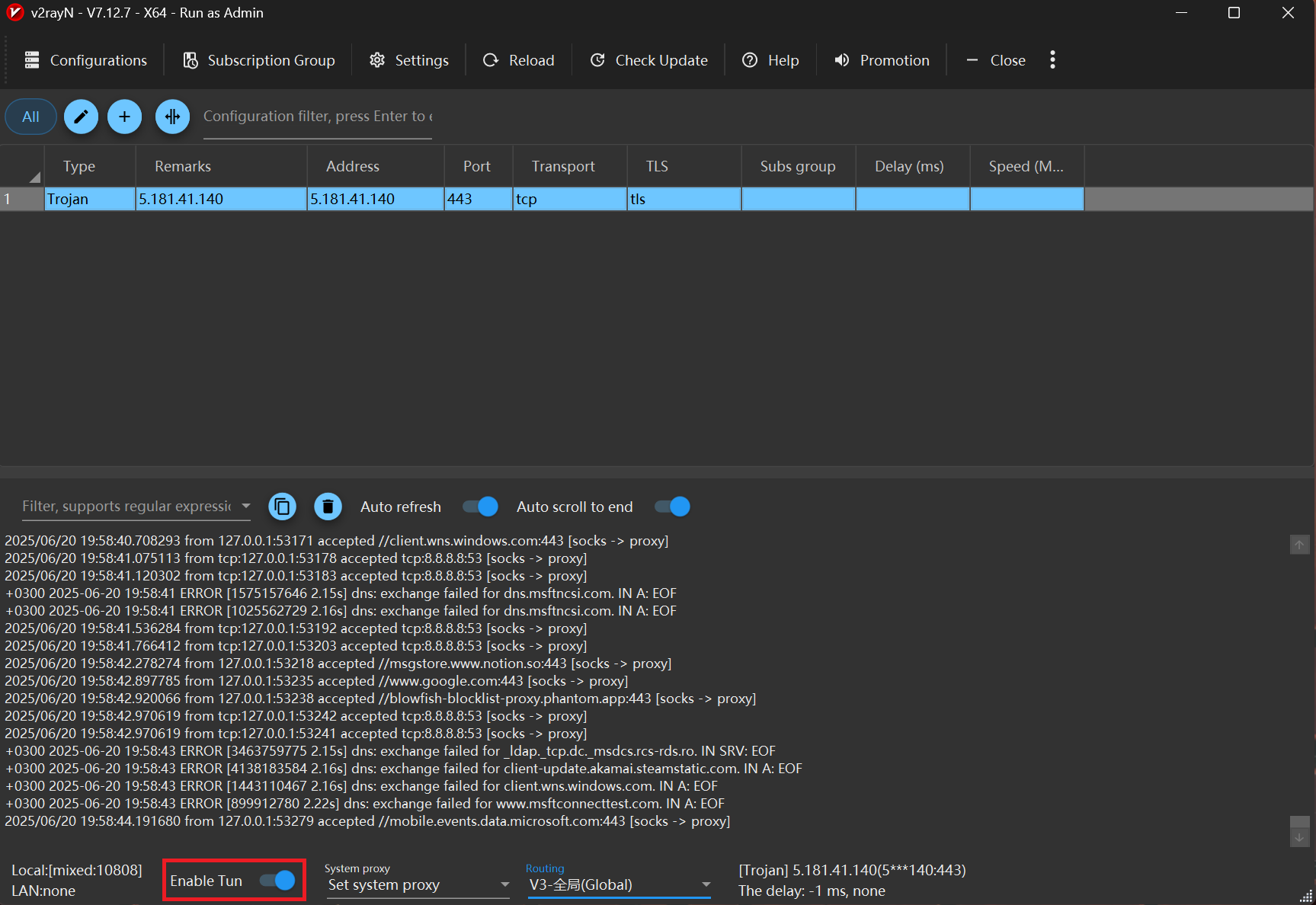
Blanket bans in June 2025 illustrate how quickly state censorship can adapt, but two proxy protocols—Shadowsocks and Trojan—still manage to keep users online with steady consistency. They endure because they emulate the TLS traffic that Iran's own governmental services and business depend upon; disabling them all at once would cripple the very systems that the government needs to stay online.
Also, if you have any questions or problems during the setup of your Iran proxy, don't hesitate to contact our support team.
@2025 anonymous-proxies.net